An FBI “IIR” intelligence report, dated April 12 2012 entitled “Identification of Internet Relay Chat (IRC) Channels Used by Anonymous Members, as of 12 April 2012” surfaces a dicey realm between US military & intelligence and electronic activists. The full report is at scribd.com/doc/246922867/FBI-FOIA-IRC-Chat-Channels-used-by-Anonymous // (Mobile)
FBI FOIA IRC Chat Channels used by Anonymous by Smiley Hill
A tiny peek into a huge deal: the potential fracas between assorted would-be American military cyberwar commandoes and international (and domestic!) computer activists. This lower-level report (Unclassified//For Official Use Only) (U//FOUO) perhaps is more interesting for its “metadata” rather than thoroughly censored content. Below I also included some other domestic military operations documents below to draw a wider context than just this “cyberwar” stuff, as Ferguson has prompted Gov. Nixon in Missouri to activate the state militia, it’s good to read up on what federal legal doctrine for “civil disturbances” is.



Such recipients: In order, it says it is from “DIRECTOR FBI” to:
All FBI field offices
INFO AFOSI DET 331 Andrews AFB Maryland, Headquarters Air Force Office of Special Investigations (also cited in this case http://www.dod.mil/pubs/foi/homeland_defense/intelligence/EFF_vs_DOD_Bates_997_1096.pdf )
CDR USSTRATCOM Offutt AFB Nebraska, Strategic Command commander
CDR USTRANSCOM Scott AFB Illinois, United States Transportation Command commander
CDR1STIO Ft Belvoir Virginia, First Information Operations Command commander – https://www.1stiocmd.army.mil/ (wat? “CDR1STIO” pops in a bunch of other FOIA’d IIRs as well if you googlize it)
CIA WASHINGTON DC – always down for a good time
DEPT OF HOMELAND SECURITY WASHINGTON DC – yes, this hot info wasn’t stovepiped away from rivals
DEPT OF JUSTICE WASHINGTON DC – fetching banhammer
DEPT OF STATE WASHINGTON DC
DIA WASHINGTON DC – Defense Intelligence Agency which is huge and low profile – http://www.dia.mil/
DIRNAVCRIMINVSERV – Probably HEADQUARTERS. NAVAL CRIMINAL INVESTIGATIVE SERVICE.
DNI WASHINGTON DC – Director of National Intelligence. (Clapper at the time)
HQ AFOSI Andrews AFB Maryland – Air Force Office of Special Investigations. Tip, if you have some message for them, use their unencrypted contact form to let them know about fraud or etc. What could possibly go wrong? > http://www.osi.af.mil/main/contactus.asp
HQ NORAD USNORTHCOM INTEL PETERSON AFB – US Northern Command located near Colorado Springs was created as Dept of Homeland Security’s military counterpart for “Homeland Defense”, an elastic concept extending Pentagon involvement with “critical infrastructure,” namely the machinery of major corporations. They also revised “GARDEN PLOT” into CONPLAN 3502 Civil Disturbance Operations,” relevant in a Ferguson type context under federal mobilization. (see 2010 story) They were also written into Superman’s plot.
JOINT STAFF Washington DC – J2 – Director for Intelligence (J2) on the Joint Chiefs of Staff (now this guy)
JWAC DAHLGREN Virginia – Joint Warfare Analysis Center a “premier science and engineering institution” under Strategic Command (USSTRATCOM), which also hosts Cyber Command. see http://www.stratcom.mil/functional_components/
NGA HQ Bethesda Maryland. The National Geospatial Intelligence Agency, like DIA, is up to a lot of things off the radar. They have domestic satellite spying (GEO INT) responsibilities at National Special Security Events which require a special domestic military intel privacy waiver. http://www.stratcom.mil/functional_components/ . Big spenders.
NSA FT GEORGE G MEADE Maryland – National Security Agency at the oddly spelled out Ft Meade. I wonder how many land in this inbox – and how many times “George G” is stored in their databases.
US SECRET SERVICE WASHINGTON DC
USCYBERCOM FT GEORGE G MEADE Maryland – Cyber Command in ur router, sniffin ur packets
WHITE HOUSE SITUATION ROOM WASHINGTON DC.
BT . … I am fairly sure this is a closing list tag like </UL>
////
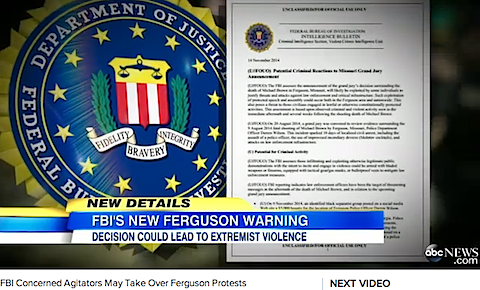
Serial IIR 4 213 4003 12, “WARNING (U): This is an information report, not finally evaluated intelligence. It is being shared for informational purposes but has not been fully evaluated, integrated with other information, interpreted or analyzed. Receiving agencies are requested not to take action based on this raw reporting without prior coordination with the FBI. Unless a conviction in a criminal proceeding occurs, a presumption of innocence exists for any person being reported on in this IIR.” Declassification date appears 20370607, as this hot stuff needs to lay low for a couple more decades.
What is an IIR? It is pretty low level stuff for the FBI. For a bit of info see FBI Intelligence Information Report Handbook | Electronic Frontier Foundation. That document interestingly, at the very end includes a statutory info pipeline from Grand Jury operations to various feds. Patriot Act Section 203(a)(1)( C )(i)(V) certainly makes for an industrious star chamber circuit, but they don’t want grand jury info going out in IIRs without asking the HQ attorney.
This document was obtained by Smiley Hill via FOIA. Please follow https://twitter.com/smilyus for more smileable FOIAs on a regular basis.
////
The use of the military – and these contractors in the game now – to police corporate systems labeled as Critical Infrastructure is significant. After all, Missouri Gov Nixon just activated the state militia because of Ferguson.
In the recent FBI writeup freeking out about Ferguson protesters, I took the “critical infrastructure” references to allude to authorizing military activity around corporate electronic assets that might get poked at by angry activists.
“The announcement of the grand jury’s decision … will likely be exploited by some individuals to justify threats and attacks against law enforcement and critical infrastructure,” the FBI says in an intelligence bulletin issued in recent days. “This also poses a threat to those civilians engaged in lawful or otherwise constitutionally protected activities.”
////
Background on Executive Order 13636:
Feb 2013: Executive Order — Improving Critical Infrastructure Cybersecurity | The White House
CRS analysis on Executive Order: http://fas.org/sgp/crs/misc/R42984.pdf
Feb 2013: Pentagon will require security standards for critical infrastructure networks – Nextgov.com
This is actually a word? Cyberinfrastructure – Wikipedia, the free encyclopedia
USA TODAY: Feb 2013: Cybersecurity executive order fosters information sharing for greater good
As for the legal ramifications of domestic military operations and targeting electronic activists with tools like STRATCOM / CYBERCOM retain for battling Al Qaeda servers or whatever, most people say “But, Posse Comitatus!” In reality a vast area of domestic military operations has been expanded and operated by JAGs. See : www.loc.gov/rr/frd/Military_Law/pdf/operational-law-handbook_2012.pdf
This Domestic Operational Law Cyber Realm has a Handbook, People!

The domestic version of this JAG manual is extremely recommended reading for everyone. See Domestic Operational Law Handbook for Judge Advocates 2011 | Public Intelligence.
Also the newer 248 page Domestic Operational Law Handbook for Judge Advocates 2013 | Public Intelligence is available. You will definitely know moar about WTF is up with weird meshes of civilian/military authority in the US by skimming over this.
PI highlighted a bunch of good 2011 stuff, since we are talking Ferguson anyway, it’s worth noting again:
G. The Department of Defense Civil Disturbance Plans
Formerly, DoD’s Civil Disturbance Operations (CDO) plan was known as “GARDEN PLOT.” Since the creation of the Department of Homeland Security and USNORTHCOM however, DoD has delegated to geographic combatant commanders responsibility for developing CDO Contingency Plans (CONPLANs). These geographic commanders’ CONPLANs provide guidance and direction for planning, coordinating, and executing military operations during domestic civil disturbances.
1. Civil Disturbance Operations Mission
Broadly stated, the CDO mission assists civil authorities in restoring law and order in the United States and its territories.58 This mission statement, while not duplicating the language in the Insurrection Act allowing for the use of federal forces to “suppress” insurrection, provides wide latitude to the President to use federal forces to assist civil law enforcement in “restoring” law and order.
The restoration of law and order must be distinguished from the preservation of law and order. CDO mission statements do not allow the joint civil disturbance task force commander to undertake preservation missions. It is generally agreed that missions to restore law and order include dispersing unauthorized assemblages, patrolling disturbed areas, maintaining essential transportation and communications systems, setting up roadblocks, and cordoning off areas. Care should be taken before a military commander accepts missions that are routine maintenance of civil order.
2. Combatant Commanders’ CONPLANs
The CONPLANs provide the basis for all preparation, deployment, employment, and redeployment of Department of Defense component forces, including National Guard forces called to active federal service, for use in domestic civil disturbance operations, in support of civil authorities as directed by the President. The concept of a civil disturbance operation is multi-phased: Phase 0, Shape; Phase I, Anticipate; Phase II, Respond (deployment can occur in either Phase I or Phase II); Phase III, Operate; Phase IV, Stabilize; and Phase V, Transition (redeployment). Prior to deployment, military forces maintain five preparedness postures, called Civil Disturbance Conditions (CIDCONS) in order to alert and react to potential civil disturbance operations. Changes in the CIDCON level are directed by the JDOMS.
…
3. The Standing Rules for the Use of Force for U.S. Forces
Civil disturbance operations are conducted in accordance with Appendix L of the Standing Rules of Engagement/Standing Rules for the Use of Force for U.S. Forces (SRUF). Guidance on how and when forces can use force in a CDO mission are detailed in that annex. Although the CJCSI is classified, Annex L is not and can be shared with our mission partners.
a. Custody and Detention
All apprehensions should be made by the civil police force unless they are not available or require assistance. Military forces have the authority to detain rioters, looters, or other civilians committing criminal offenses. Civilians taken into custody should be transferred to civilian law enforcement authorities as soon as possible.
All members of the force must remember that state and federal criminal law and procedure govern apprehension. Apprehension is justified only on the basis of probable cause to believe that an offense has been committed and that the person to be apprehended committed the offense. Soldiers should not question detainees beyond basic pedigree such as name and address. If formal questioning of an offender is necessary, civilian police should conduct the interview. If civilian police are not available, CID agents or military police may conduct interviews only if the interview is essential to the civil disturbance mission. Actions taken by Soldiers that do not conform to criminal law constitutional standards could jeopardize future prosecution and subject Soldiers and their Commanders to criminal and/or civil liability.
b. Search and Seizure
CDO CONPLANs anticipate that military forces will generally not be involved in searches unless there is “an immediate danger of violence, destruction of evidence, or escape of violent persons unless the search is conducted without delay.” In all other cases, local authorities should conduct searches. When required to perform searches, federal armed forces may conduct warrantless searches under the same constitutional parameters imposed upon law enforcement officials. Joint Civil Disturbance Task Force forces conducting a warrantless search will fully document the reasons for the search as soon as is reasonably convenient.69 Generally these searches are limited to the following incidents.
(1) Stop and Frisk
If there is a reasonable suspicion based upon articulable facts that a person has committed, is committing, or is about to commit a crime, that person may be temporarily stopped and questioned about his activities. The stop must be limited in duration to that which is reasonably necessary to investigate the suspicion. If there is a reasonable suspicion based on articulable facts that a person is armed or is carrying instruments of violence and that the individual presents an immediate risk of harm, members of the armed force may conduct a “frisk” (an external “patdown” of the clothing) for weapons. Any weapons found during a frisk may be removed from the individual and seized.
(2) Search Incident to Lawful Apprehension
A person lawfully detained may be searched for weapons or destructible evidence. A search for weapons or destructible evidence may also be conducted in the area where the detained person could reach with a sudden movement to obtain a weapon or destroy evidence.
(3) Exigent circumstances
Military forces assisting law enforcement may make a search without a warrant when they have reason to believe (probable cause) that weapons, objects related to criminal activity, or persons believed to have committed an offense, are in the place to be searched; and they have reason to believe that the delay necessary to obtain a search warrant would result in removal of the weapons or destruction of the objects related to criminal activity. For example, Joint Civil Disturbance Task Force forces may stop and search an automobile without a warrant when there is reason to believe that the automobile contains weapons or instruments of violence and/or contains an individual reasonably believed to have committed violence.
(4) Emergency
Military forces in a civil disturbance operation may make an immediate entry into a building when there is reason to believe that entry is necessary to prevent injury to persons, serious damage to property, loss of evidence, to protect public safety, or to render aid to someone who is in danger.
(5) Hot pursuit
Military forces pursuing a person who they have reason to believe has just committed a serious crime, may enter a vehicle or building believed to be entered by the suspect and search the building or vehicle for the person or any weapons that might be used to further his escape.
(6) Plain View
During the course of otherwise lawful activity, military forces may seize any unlawful weapons or objects related to criminal activity which they observe in plain view. When conducting warrantless searches that require a probable cause determination, military forces can obtain advice from a judge advocate; however, the probable cause determination must be made personally by the individual desiring to conduct the search.
If a search warrant is required, local civil authorities should obtain judicially issued search warrants. If local civilian authorities are not available, judge advocates need to be prepared to provide advice on probable cause to military authorities before they approach a local judge or magistrate for a search warrant.
When feasible, all searches conducted by military personnel will be conducted by two personnel with the actual search performed by someone of the same sex.76 A hand receipt or some similar document should be prepared when items of personal property are seized from an individual.
c. Confinement Facilities
The Joint Civil Disturbance Task Force should not operate a detention facility. Any person apprehended should be turned over to the police for detention. Military correctional facilities cannot be used to detain civilians. If available civilian detention facilities cannot accommodate the number of detained persons who are awaiting arraignment, the Joint Civil Disturbance Task Force commander must seek the approval of the SCRAG and Combatant Commander to set up a temporary detention facility.
Should the Task Force be required to operate a detention facility, the detention facility standards and operations should conform, to the maximum extent possible, to current DoD confinement facility operations and will be under the professional supervision and control of Military Police personnel. The establishment and operation of military detention facilities is a temporary expedient and is authorized only until such time as the custody of detained persons can be transferred to civil authorities.
d. Riot Control Agents
Normally, for CDO the deployment and use of riot control agents is allowed as a matter of U.S. policy. However, initial approval authority for its deployment and use may be retained at a level higher than the Joint Civil Disturbance Task Force Commander and may require a specific request.
This is not the same as a state-level activation, but it is the doctrine that is crafted at the federal level these days so I think it’s pretty relevant to Ferguson.

The federal government hasn’t taken kindly to people that expose these types of relationships. Barrett Brown’s sentencing just got delayed again – but at least the Barrett Brown Review of Arts and Letters and Jail is awesome. For more info FreeBarrettBrown.org.
EXCLUSIVE: Such Critical Infrastructures: FBI feeds Anonymous IRC channels to CIA, Pentagon intel, NSA, NORTHCOM in 2012 Intel memo
HongPong
Wed, 19 Nov 2014 06:33:15 GMT